Every file and every program leaves traces in your system: It accesses other files, uses Windows resources, makes entries in the registry, and possibly installs additional software.
In the best-case scenario, you will only clutter up your Windows if the software’s uninstall routine does not delete all associated files and registry entries. In the worst-case scenario, malware will infect your system or ransomware will encrypt your files.
If you want to try out new programs or open unknown files, it is best to do this in a particularly secure environment that is separate from the running system: This is exactly what a sandbox offers.
If you open a program in a sandbox, it works as expected, but cannot make any permanent changes to the system or access resources outside its environment — the sandbox prevents this, redirects access, and deletes all activities of the program and itself when you close it.
With a sandbox, you can therefore try out new software or install programs from dubious sources with less risk, surf potentially unsafe websites, and keep your system clean.
We will show you various ways of setting up and using a suitable sandbox for programs and files under Windows: These range from Windows on-board resources and virtual systems to browsers and programs with their own sandbox function.
We describe the Sandboxie-Plus software in particular detail — the simplest and most practical sandbox solution for most users.
Sandbox for the browser
You probably already use a sandbox: Current browsers such as Chrome and Firefox use this protection technology.
They rely on Windows security mechanisms: This has the advantage that they can guarantee a high level of protection without having to use a lot of resources, which could result in websites opening slowly, for example.
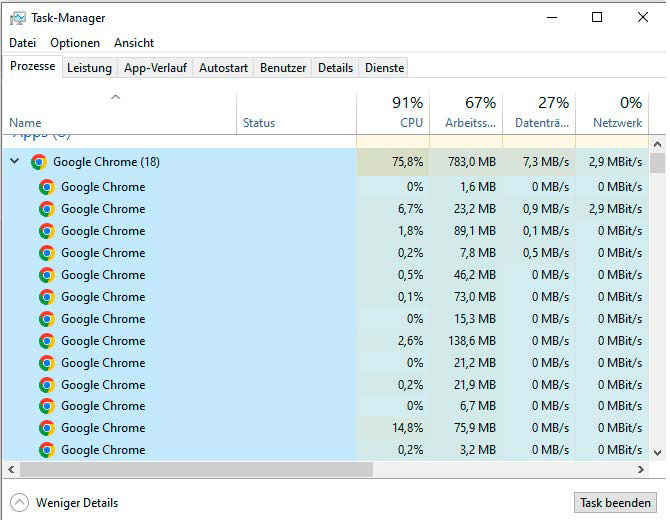
Like most browsers, Chrome opens each tab in its own isolated process, which can be seen in the Task Manager. All websites are shielded from each other.
IDG
Each browser tab is opened in its own sandbox. This prevents Chrome and others from automatically downloading programs on a website or running malicious scripts.
This process also protects against attacks that are executed via a website without an antivirus program raising the alarm (zero-day exploits).
Each tab of the browser runs as an isolated process and has no access to other tabs or the system. It also starts with very limited rights — which is why you usually have to authorize a website’s access to the computer camera, for example.
In addition, the separation of the individual tabs should mean that the crash of a website does not paralyze the entire browser, but only the corresponding tab.
How and whether the browser sandbox works can be observed in the Windows Task Manager: Under “Processes” you can see that numerous other processes are running under the “Google Chrome” entry — these are the separate sandboxes of the individual tabs.
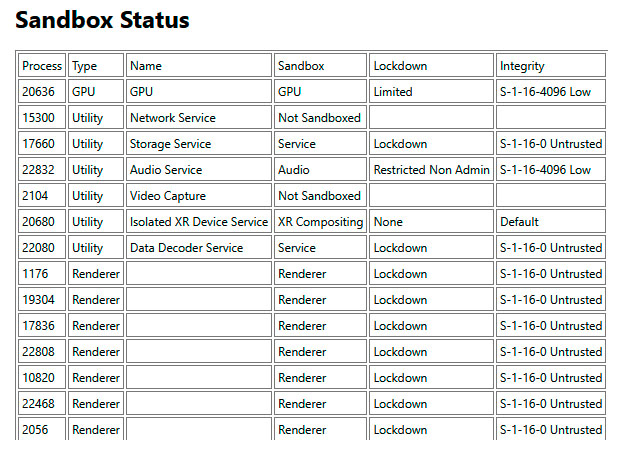
You can find out more details by entering the command
chrome://sandbox/in the browser address bar: The tabs here are called “Renderer” — this is the function that displays web pages. Each should also appear in the “Sandbox” column and in the next column with the note “Lockdown.”
Like the “Untrusted” entry to the right, this means that this process has very few access rights to the system.
IDG
Nevertheless, you should always update your browser, as hackers often try to exploit the sandbox via other security vulnerabilities in order to give scripts and programs on a website more access rights.
Programs with a built-in sandbox
Windows also uses a sandbox for certain programs: Apps from the Microsoft Store — the so-called UWP apps (Universal Windows Platform) — run in an isolated process with reduced rights.
This means they can be uninstalled without leaving any residue. In many cases, you must also authorize them to access files or hardware such as the camera or microphone.
However, only a few users use UWP apps. The more frequently installed standard programs — the so-called desktop apps — run without a sandbox and rights restrictions.
You also give many UWP apps certain rights during installation. You can check what these are before installation on the app page in the Microsoft Store under the entry “This app can” and after installation in the Windows settings under “Privacy > App permissions.”
You can revoke these rights there — although this often means that the app no longer functions correctly.
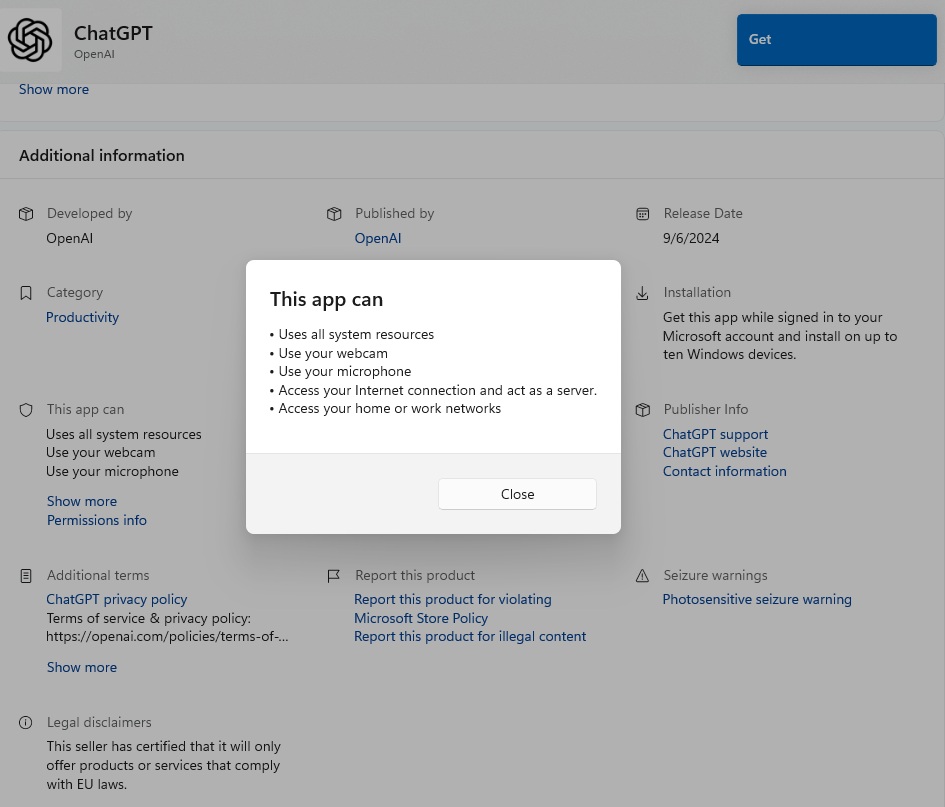
Programs from the Microsoft Store run in an isolated environment: However, they often request numerous rights during installation, which undermine this protection.
Foundry
From version 24H2, Windows 11 also supports a sandbox function for normal programs — Win32 App Isolation. However, manufacturers must incorporate this into their software for the protection to work.
Acrobat Reader offers a secure sandbox function for PDF documents: If you receive a PDF as an attachment from an email or an insecure source, you can prevent code contained in the document from being executed or you from being taken to a nefarious website when you click on a link in the PDF.
To use the PDF sandbox, go to “Settings > Security (advanced)” in the Reader menu and activate the “Enable protected mode on startup” option.
Additional protection is provided by the “Protected view” below, where you can choose whether it should apply to all PDFs or only to those from insecure sources. The Reader then opens the PDF in read-only mode, which means it cannot be filled in and usually cannot be saved or printed.
The small open source tool Sandboxie-Plus is ideal for running all suspicious files and programs in isolation. You install it as usual under Windows and can then start the desired content directly in a sandbox container.
The complete range of functions of Sandboxie-Plus costs $40 per year: You can pay the programmer directly via Paypal or you can buy a supporter certificate on the website.
For use on a home computer, however, the free basic functions, which we present below, are sufficient.
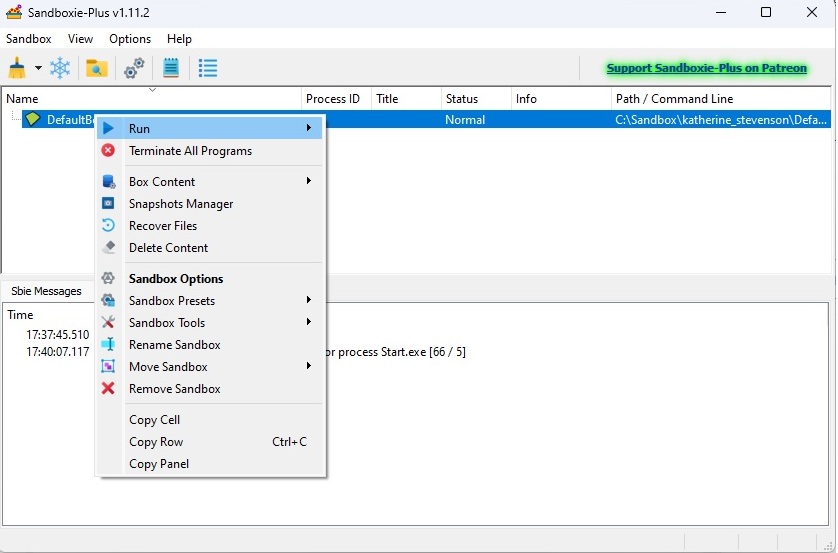
With Sandboxie-Plus, programs can be started in an isolated environment: They cannot access the system and can be removed without leaving any residue.
Foundry
Sandboxie-Plus is available in versions for standard Windows and for Arm Windows.
The tool can also be installed as a mobile app on a USB stick. After installation, you will be greeted by a setup wizard where you first select the option “Personal, for non-commercial use” for the free functions.
In the next window, you can obtain a so-called evaluation certificate by clicking on the red, underlined text: This allows you to test the software with all functions for 10 days.
Otherwise, click on “Next.” For the user interface, you can choose between an expert and a beginner mode as well as a light or dark mode for the display.
It is best to accept the default settings and click “Next” again. Finish setting up the software in the last window by clicking on “Finish.”
In the following window for the “Global settings,” you do not need to adjust anything and click on “OK.”
Running risky programs in Sandboxie-Plus
Sandboxie-Plus starts with a two-part interface: At the top you will see the entry for a “DefaultBox.” You can start suspicious programs in this box. In the lower window, the tool logs all actions and settings.
The user interface can also be called up by right-clicking on the tool icon in the system tray and selecting “Show / Hide.”
To start software safely in a sandbox, click on “Sandbox > Run in sandbox.” Confirm the settings in the next window with “OK.”
Another window then appears: Enter the name of the software that you want to start in Sandboxie-Plus and confirm with “OK.” If you do not know the exact name or the tool cannot find a program that matches your input, you can call up the software directly with the Explorer via “Search.”
This start procedure is recommended for programs that you have installed but want to start again in the secure environment — for example, your web browser: If you call it up again in the sandbox, you can use it to visit suspicious websites without risk.
The program then starts: The corresponding EXE file appears in the top window of Sandboxie-Plus.
You can recognize that software is running in the sandbox by two features: Its name in the program window begins and ends with a diamond symbol — for example, if you open the Chrome browser in the sandbox and drag the mouse to its icon in the taskbar, it will say [#] New Tab – Google Chrome [#].
If you move the mouse to the top edge of the program window, a yellow frame appears. There is also a window finder in Sandboxie-Plus under “Sandbox — Is the window in a sandbox?”
There, click on the circle in the small program window on the left, hold down the left mouse button and release it in the window of the program whose status you want to check: The answer to the question will then appear in the window finder.
Sandboxie-Plus is also entered in the context menu of Windows Explorer: You can then call up the desired program with a right-click and the command “Start Sandboxed.”
For example, software that you have just downloaded can be installed in the sandbox by starting the corresponding EXE or installation file with Sandboxie-Plus.
It is advisable to run each program and each file in its own sandbox: When starting via Sandboxie-Plus or the context menu, select the entry “Run in a new sandbox” in the next window and then “Standard sandbox.”
You can also give each sandbox a meaningful name here.
Important programs can be started particularly quickly in Sandboxie-Plus, for example your browser, your email program, or Windows Explorer: Click on an existing sandbox in the top right-hand corner of the tool window.
Then select “Start > Standard programs” and then the desired software.
Open and check suspicious files
Like programs, individual files can also be opened in an isolated sandbox. Sandboxie-Plus starts the default program for this file — for example Word for a DOCX file.
If the program crashes, change a setting in Sandboxie-Plus: Open the file in a new sandbox as described. In the window in which you select “Standard Sandbox” as the box type, tick the “Configure advanced options” option at the bottom right.
After clicking on “Next,” select “Version 1” for “Virtualization scheme,” click on “Next” several times, and finish with “Finish.”
With Sandboxie-Plus, you can tell whether a software really works in the sandbox by the yellow frame around the program window and the hashtags before and after the program name at the top.
IDG
Important: A program that you start in the sandbox can only read files outside the sandbox and cannot change them. If you open a file within the sandboxed software, it can be changed, but this has no effect on the original file:
For example, if you start Outlook in the sandbox and delete an email there, it will still be there when you open Outlook normally.
Emails with suspicious attachments can be examined in this way: You open your mail program in the sandbox and open the attachment. If it seems suspicious or comes from an unexpected sender, delete the sandbox and then delete the email in your normal email program without opening it or looking at the attachment.
Sandboxie-Plus isolates programs and files by creating separate directories for them: These are located in the program directory “C:\Sandbox\username,” where there is a separate folder for each sandbox.
The tool also stores changes made by the isolated program in the registry there. In this way, no traces remain in the system when you delete the corresponding sandbox.
You can do this by right-clicking on the desired sandbox in the upper window of Sandboxie-Plus and selecting “Remove sandbox” from the context menu. If you want to keep the sandbox but close the programs running in it, select the “Close all processes” command in the context menu.
Alternative: Virtual PC
A virtual PC (VPC) is also suitable for starting risky programs or opening suspicious files. Windows includes the Windows Sandbox for this purpose. It is a VPC based on Microsoft’s Hyper-V virtualization software, but is only included in Windows Pro.
You also need to install it first: You do this via the Control Panel and “Enable or disable Windows features.” Select the “Windows Sandbox” entry there and restart the computer.
You will then find the program as “Windows Sandbox” in the selection of installed apps. After starting, another Windows desktop opens as the user interface of the virtual PC: You operate this as you would your normal system — so you can install and try out programs in the Windows Sandbox.
You can copy and paste suspicious files from the main system to the virtual Windows.
Since the Windows 11 update 22H2, the VPC also supports a restart that preserves its data and applications. However, this only applies if you only restart the sandbox: If you close the VPC window or restart the main system, the contents of the sandbox will be deleted.
If you are using Windows Home, you can use free virtualization programs such as Virtualbox for a VPC. However, the virtual computer needs an operating system — if it is to be Windows, you will need an additional lisence for this.
A VPC is largely isolated from the main system and is a secure test environment.
Compared to Sandboxie-Plus, however, it is oversized if you only occasionally want to try out unknown programs or open suspicious email attachments: You have to install your own operating system in the VPC, which places correspondingly high demands on your computer’s hardware.
This applies on the one hand to CPU performance, but above all to RAM: You should provide at least 4GB of RAM exclusively for the virtual system; more RAM significantly increases the ease of use of the VPC.
It is also not ideal for a quick file check: You have to start the VPC like a normal system and wait until the virtual Windows is ready for use.
This article originally appeared on our sister publication PC-WELT and was translated and localized from German.